Vulnerabilities are part and parcel of the software development life cycle. If left untreated, they can expose your application to malicious attacks, which can be detrimental to its functioning and reliability. To avoid severe damage and complications that arise from having the vulnerabilities exposed, it is good practice to set up a vulnerability management system.
Vulnerability management is a practice that teams should integrate into the larger development process as it helps keep the software secure. In this article, we examine security vulnerability management with a focus on identifying and fixing vulnerabilities early in the development life cycle.
What is vulnerability management?
A security vulnerability is a weakness or flaw in the code that exposes the software to external attacks, which can gain access to the system and steal information or damage it from within. They can be located in any part of your software, whether it is in the infrastructure layer or in the application itself.
Although related, these are different from threats and risks. Vulnerabilities can be exploited to launch attacks, and threats are processes that exploit the vulnerabilities. Risks constitute the consequences of such exploitation, i.e., the damage or harm caused to the software.
Security vulnerabilities, if not caught in time, can cause great harm to the software. For this reason, software development teams must treat vulnerability management as indispensable to their workflows. Additionally, attackers often make use of multiple vulnerabilities to launch a single attack. So, reducing the number of exploitable vulnerabilities is more likely to hinder their attempts.
Security attacks also result in outages or the slowing down of services as the team scrambles to do damage control. To make matters worse, they put user data at severe risk. This does not meet users’ expectations for application reliability and availability and can further harm the business. It is in the team’s best interest, therefore, to ensure that the risks associated with vulnerabilities are minimized to the greatest extent possible.
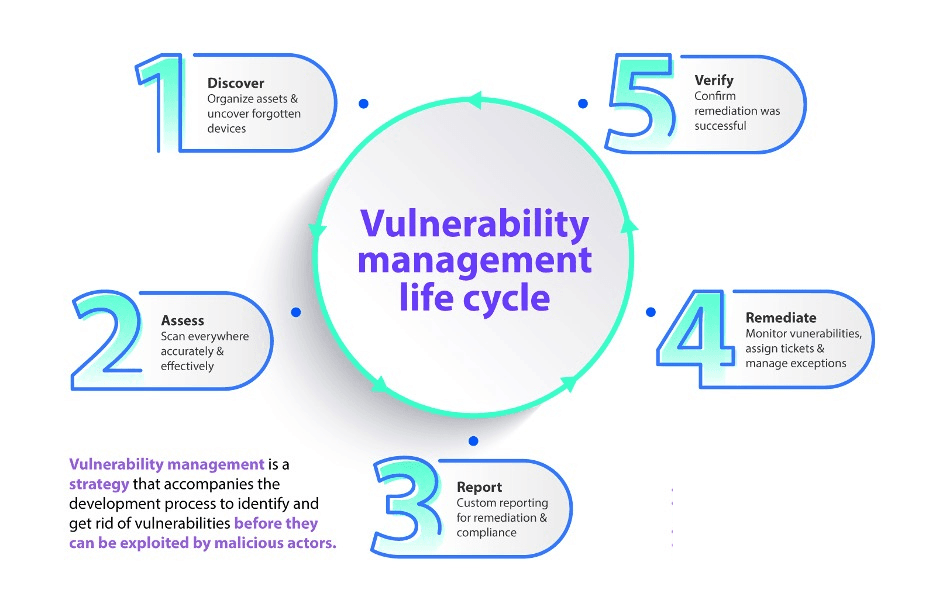
Vulnerability management is a strategy that accompanies the software development process to identify and get rid of vulnerabilities before they can be exploited by malicious actors. Teams benefit from establishing best practices and standards surrounding vulnerability management. It reduces confusion and makes it more likely for developers to abide by them when building the software. Rather than as a one-time task, it should be treated as a continuous process that helps developers prioritize security in their work and meet novel challenges that surface one after the other. There is no denying that this is an arduous undertaking, but it is ultimately worth it.
Why is early vulnerability management important?
It does not suffice to scan for vulnerabilities as an afterthought. Vulnerability management must be intentionally integrated into the development process such that it can be executed in the most effective way. One way to ensure this is by pushing developers to consider vulnerabilities as a serious threat in the early stages of the software development life cycle.
Why is this important? Too often, developers find themselves putting together patches or security updates at the last minute or after a vulnerability has been exploited. The tight deadlines that are characteristic of the development process lead them to focus on shipping the application as fast as possible, putting security on the back burner. This increases the chances of the software being susceptible to attacks. Software security demands a proactive, not reactive approach. The latter can be limiting, as last-minute make-shift solutions often do not contribute to a larger, long-term security strategy.
It is also more challenging and time-consuming for developers to fix the vulnerabilities closer to the production or deployment stages. If the code they are tackling was written at the beginning of the development process, they may find it difficult to revisit it and spend more time making sense of what is going on.
If instead developers center security in their coding practice, they can locate any security bugs present in the code well in advance. This gives them ample time to troubleshoot and come up with a robust solution. Over time, as an organization’s vulnerability management practices strengthen and become more efficient, the amount of time taken to fix a security issue also reduces. Time is saved, developers are more productive, and the end product is more reliable. To this end, we recommend equipping developers with the appropriate tools and know-how. In the rest of this article, we explain how you can go about doing the same.
How can you motivate developers?
To ensure that vulnerability management begins early in the development process, you have to get developers to prioritize it as an integral part of their workflow. In addition to pointing out that the number of vulnerabilities they will have to fix later will be reduced, here are a few ideas to get you started:
Education: Helping developers understand how their code contributes to the security of the software is crucial. Also, provide your developers with the knowledge required to write code that is not susceptible to vulnerabilities. One way to go about this is to integrate a real-time feedback or testing process when the developer is coding the software. This way, they can learn in a practical setting and are encouraged to fix vulnerabilities. This will significantly reduce the number of vulnerabilities that will surface at the time of testing.
Collaboration: A big part of bringing vulnerability management to developers is to encourage collaboration with security and testing teams. Developers may initially feel lost and will benefit from working together with fellow employees who can offer guidance. They can also set standards that make it easier for developers to understand expectations and work towards meeting them.
Automation: Introducing developers to the appropriate tools will also make the practice seem less intimidating or inconvenient. They will not be overburdened or have to manage vulnerabilities inefficiently. It is important to invest in tools that will support the developers instead of making things harder for them.
How can you run vulnerability management?
How can your developers effectively manage vulnerabilities earlier in the process? First, you need to figure out what vulnerabilities exist in your codebase and prioritize them depending on how much risk they pose. To do this, invest in vulnerability management tools. Then, fix the security bug and document it. In this section, we look at these steps in greater detail.
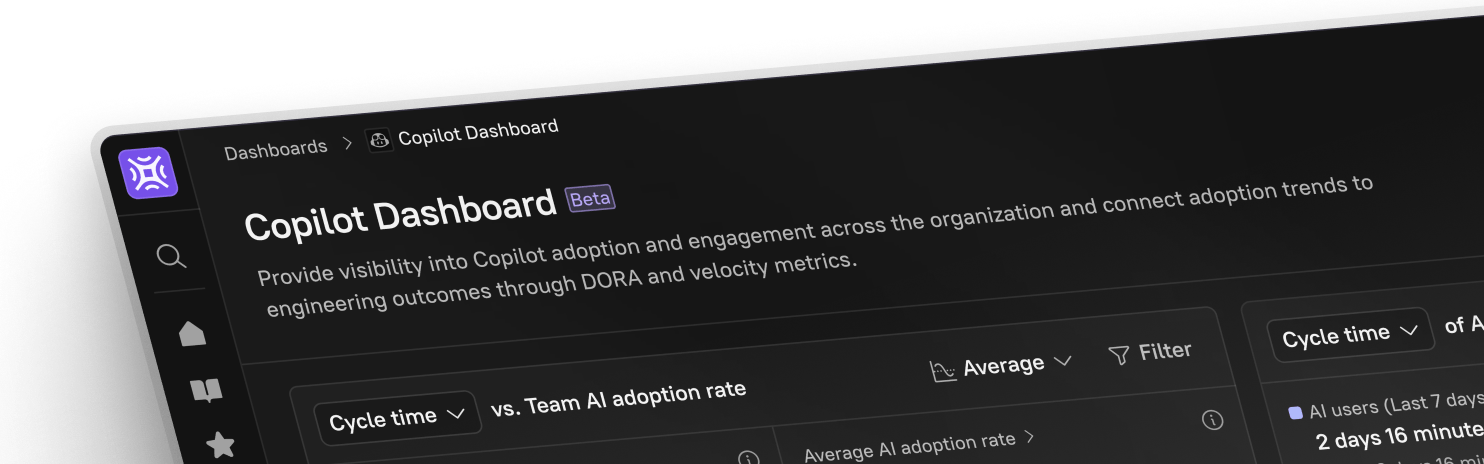
Identify the vulnerabilities
First and foremost, survey your architecture for any vulnerabilities. There is no shortage of vulnerability scanners in the market. They run tests against your system and networks, looking for common security issues in the code.
Identify the different vectors that are possible for your application. For example, if you are containerizing using Docker or Docker images, you want to scan the actual file system and the operating system that you're running. A container scanning tool will come in handy here. If you are interested in doing runtime, penetration, crowdsourced, or bug testing, invest in the appropriate tools that will help you run those tests.
Penetration testing, for instance, is a simulated attack you launch on your software to identify vulnerabilities in the system that can be exploited. It is a form of ethical hacking carried out internally or by trusted third parties that mimic the anticipated actions of actual hackers interested in gaining unauthorized access to your software. It is a proactive way of keeping your software secure by catching vulnerabilities before hackers are given the opportunity to exploit them.
We also recommend doing static analysis vulnerability scanning. This will help you figure out gaps or inefficiencies in your workflow, such as whether the team is following poor practices or if the code is going to cause a buffer overflow or a memory exploit. A static analysis tool can give you relevant information concerning your code’s performance against the more objective, well-known coding best practices. Tools like SonarQube or even an open-source solution can’t assure you of a vulnerability but will be able to tell you if a particular pattern that you are using could potentially introduce a vulnerability in your code. Our integration with Mend allows you to identify security weaknesses and vulnerabilities and aims to automatically remediate them as far as possible.
Finally, actual package dependency scanning tools like Snyk or npm-audit are also great to use. They can inform you if there are any vulnerabilities in the packages that you depend on, which is vital information and otherwise hard to gauge for developers.
How do you use these tools?
Include scans in your CI/CD pipeline
Run the tools as part of your CI/CD process. So every time somebody opens a pull request, you want to check if that particular PR introduces any high severity vulnerabilities. If you are introducing something new during build time, block for critical or high vulnerabilities and don’t let them pass through. However, be careful not to block on medium or low vulnerabilities because that will slow down velocity. At the same time, you want to track that somewhere, so make sure you have visibility on it. Figure out how many vulnerabilities you are producing then record this data someplace and track it at a per repository level.
The same applies to running a scan on Docker when you are generating the actual image. If you are not publishing the image from your repository until master, run a Docker image scan as part of your master build.
Additionally, make sure that developers have visibility, without which they will not do anything about the results of the scan. Avoid buying a tool and having only the security team look at it. The developers need to be looking at it more frequently too.
Plan for the future
You might have run a scan and not found any vulnerabilities, but that does not mean the service is not going to have any six months from now either. Even if you are not pushing code to a repository, the library it is using could have a vulnerability down the road. So make sure you are running scheduled scans frequently that are checking and alerting the developers as and when the security status of the code changes.
Create a single pane of glass
Build a central dashboard where developers can get all the relevant information in a single place. Imagine you have a bunch of tools like SonarQube and Snyk as well as container scans and penetration tests running to make sure your code is secure. Developers are not going to log into five different tools to look at their results and will risk missing out on any vulnerabilities that need to be looked into.
For a more efficient workflow, create a central dashboard where you can get easy access to the results in the form of a single view. This helps developers figure out what needs to be done next. They can identify what parts of the microservice need work or if it meets all the organization's security standards.
Go a step further and add freshness to the dashboard. Reflect on whether the information is stale and if it continues to be valid. This will depend on whether the last scan was run six months ago or the previous week. Having outdated data can be detrimental to the development process, so set certain security standards and have mechanisms in place to consistently update the dashboard.
Sort the vulnerabilities and assets by priority
Effective management approaches also maximize efficiency. For example, not all vulnerabilities are equally at risk of being exploited. Sometimes they may even be mislabelled as vulnerabilities. So developers must prioritize and look into the vulnerabilities that pose the greatest amount of risk.
This is especially relevant for larger projects that have to manage a plethora of vulnerabilities. Vulnerability management tools aid in the process of prioritization by assigning values to each vulnerability based on the risk it poses to the software. You can take these values into account when formulating a strategy to ensure your application is secure and reliable.
You can also choose to prioritize the assets in your infrastructure. By ranking your assets according to their importance, you can make an informed decision about managing the associated vulnerabilities when dealing with a resource shortage.
Make a plan
Once you have identified the vulnerabilities and prioritized assets according to criticality and risk, document this information as well as your next steps in a plan. Clearly outline the vulnerabilities and how you intend to fix them before reintegrating the assets into your application.
Fix the bug
Once you know what needs fixing, get working on the solution. This could mean applying a patch or making changes to the code. Full remediation of each vulnerability is ideal, but the solution ultimately depends on the resources (time, money, manpower) your team has at its disposal.
If you adopt vulnerability management as an ongoing process, fixing the bugs will also become part of the developer’s workflow. It will be easier for the developer to come up with solutions while the code is still fresh in their mind. Furthermore, you can rest easy knowing that any new vulnerabilities that surface are being tackled on time and that these solutions contribute to keeping your software up-to-date.
When you are done fixing the issue, be sure to verify that the solution has, in fact, been executed and that the vulnerability is no longer a threat to the software.
Finally, make sure that you have documented the entire management process. This is useful not only for meeting compliance requirements but also to assess the efficacy and practicality of the process should you wish to make any changes to improve it in the future.
Getting started
To reiterate, visibility is essential. If developers are not looking at the services and any related vulnerabilities, then they're not thinking about or fixing them. So the more visibility that they have, the more you are fostering a culture of security first, as opposed to delegating the duties to a security team working in isolation.
You can use Cortex’s Service Catalog to create a single pane of glass for developers and give them a single security score. That way, they will know whether their services are compliant from a security standpoint. Developers no longer need to log into a range of different tools to get that visibility. Once they have the information they need, they can proceed to make changes and get rid of the vulnerabilities before moving to the next step in their development workflow. Easy access to this data allows the developers to have eyes on vulnerabilities right from the beginning and throughout the process.
To get started, we suggest looking into the tools that you would like to invest in. SonarQube and Snyk are both great options and can be integrated with your services using Cortex’s Scorecards feature.