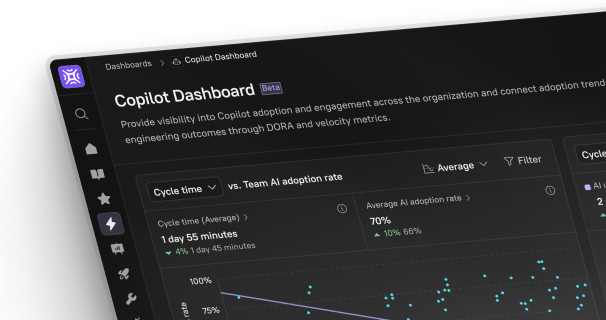
Asset attribution is an operational necessity for robust digital protection, but hasn't always been easy to achieve. Especially when software state and ownership is unknown, or inconsistent. This blog delves into the historical complexities and challenges of asset attribution for security and engineering teams and explores how Internal Developer Portals like Cortex can help.
Challenges in Asset Attribution for Security and Engineering Teams
Historically, asset attribution has posed several challenges that can complicate the security and engineering processes within an organization:
Scale and Complexity: As organizations grow, so does the complexity and number of assets they must manage. This includes everything from legacy systems to newly deployed microservices spread across hybrid environments, making it difficult to maintain a clear, updated inventory of all assets.
Dynamic Environments: In modern agile settings, assets are continuously updated, expanded, or decommissioned. Keeping track of these changes in real-time challenges traditional asset management systems, which may not update swiftly enough to reflect the current state accurately.
Integration with Security Practices: Integrating asset management with existing security practices can be cumbersome if the tools and processes are not aligned. This misalignment can lead to gaps in security coverage and increased vulnerability to attacks.
Decentralized Ownership: Particularly in larger organizations, assets may be managed by different teams with varying levels of security expertise and awareness. This decentralization can lead to inconsistencies in how assets are managed and secured, complicating efforts to enforce unified security policies.
Missing or Outdated Ownership: Aside from the challenge of tracing ownership across multiple tools, there may be situations where ownership is missing or outdated. Some examples may include physical hardware or service accounts. Not having this information on hand can have a disastrous impact on incident response timelines.
Building Asset Attribution with Cortex: An Internal Developer Portal
An Internal Developer Portal like Cortex can address these challenges effectively by centralizing software asset management and integrating it with security operations:
Centralized Asset Registry: Cortex aggregates data across tools to provide a single source of truth for all services, repos, artifacts, systems, domains, infrastructure, etc.
Always Up to Date Information: With connection to all your favorite tools including identity providers, it’s easy to query live information about each asset including details from your identity provider, git, ticketing, CI/CD, APM, logging, security, and more
Entity Verification: In situations where critical information does not exist in source systems, or is known to be outdated, Cortex enables users to set entity verification periods, wherein teams or individual owners are alerted to manually verify information on any given entity type.
Continuous Alignment to Standards: Use data from these same integrations to build rules that continuously assess alignment to standards of security, ownership, maturity, or even short term project status like package upgrades and system migrations.
Automated Updates: By automating the tracking of asset changes and integrating with CI/CD pipelines, Cortex ensures that asset records are always current, reflecting the latest deployments and decommissions. This automation reduces the administrative burden on teams and helps maintain a high level of accuracy.
Targeted Alerting: Cortex facilitates clear definitions of asset ownership and responsibilities, which are crucial for quick response during security incidents and for routine maintenance. By mapping assets to specific owners within the portal, it becomes easier to enforce accountability and ensure that security practices are consistently applied.
Incident Response & Compliance: Cortex can integrate with security tools to pull in vulnerability data, compliance status, and other security metrics related to each asset. This integration enables teams to assess the security posture of assets directly within the portal, streamlining security reviews and audits.
Enhanced Visibility and Reporting: With Cortex, organizations gain enhanced visibility into their asset landscape, which is critical for strategic planning and risk management. The portal provides detailed reporting and analytics, offering insights into asset utilization, security trends, and compliance levels.
Top Use Cases for Asset Attribution Systems
Asset attribution systems play a pivotal role in enhancing security operations across multiple teams within an organization. Here are some specific use cases that underscore the system's value:
Incident Response and Management
When a security incident strikes, it is crucial for Incident Response and Incident Management teams to swiftly identify all affected systems. These teams must quickly determine the scope of the incident and communicate with the owners of the impacted assets. This rapid response capability not only mitigates the impact of security breaches but also accelerates the recovery process by ensuring that corrective measures are timely and effective.
Vulnerability Management and Remediation
For Threat Prevention teams, the ability to trace a vulnerability back to its origin is indispensable. Whether it’s a vulnerable source code repository, an exposed endpoint, or an insecure server, knowing who is responsible for the asset allows for quick action to patch the vulnerability within service level agreements (SLAs). This capability is essential for maintaining the integrity and security of the system against external threats.
Security Architecture and Stakeholder Engagement
Security Architecture teams benefit greatly from asset attribution systems by being able to identify threat models and accountable stakeholders for services under development. This information is critical when reviewing new features or services, ensuring that security considerations are integrated into the development process from the start and that responsible parties are clearly defined.
The End Goal of Asset Attribution
The ultimate objective of implementing an asset attribution system is to provide security engineers and other stakeholders with the ability to efficiently query and retrieve ownership information about any asset within the organization. Essential questions that can be answered through the system include:
Who owns service X? This helps in directly contacting the responsible party for any service-specific issues or queries.
Who owns the server at address 1.2.3.4? Quick identification of server ownership aids in rapid response to security incidents affecting specific servers.
Who owns the code in XYZ git repository? This is crucial for addressing vulnerabilities or updates in the codebase.
Who are the security champions of that service? Understanding who is responsible for the security oversight of each service ensures accountability.
What is a service’s criticality level? Knowing the importance of each service based on user data sensitivity and usage helps prioritize security efforts.
What’s their security posture? This involves assessing how robust the security measures are for a service, considering factors like threat model maturity and vulnerability findings.
These capabilities highlight the significant role of asset attribution in not only responding to incidents and managing vulnerabilities but also in planning and securing future developments in an organization's digital landscape. By enabling detailed and quick access to essential asset information, organizations can ensure that their security measures are both proactive and reactive, safeguarding their operations against a wide range of security threats.
Conclusion
While asset attribution is inherently challenging due to the scale, complexity, and dynamic nature of modern engineering environments, solutions like Cortex can transform these challenges into opportunities for enhanced security and efficiency. By leveraging a centralized developer portal, organizations can ensure that their asset attribution efforts are as robust as their development ambitions, ultimately leading to a more secure and resilient digital infrastructure.
See it for yourself: book a custom demo to see Cortex in action.